What is ‘Essential Eight’?
The Essential Eight is a set of cyber security strategies developed by the Australian Signals Directorate (ASD), through the Australian Cyber Security Centre (ACSC) to help protect organisations from cyber threats.
The Essential Eight Maturity Model is vital for business as it helps to protect them from cyber threats, which can have serious consequences, reputational harm, and/or financial loss.
Why is Essential Eight compliance important?
Some of the reasons why the ASD’s Essential Eight compliance is important for business:
- Cyber threats are becoming more common: As technology becomes more prevalent in our daily lives, cyber threats are becoming more common and more sophisticated. Businesses need to take steps to protect themselves from these threats.
- Cyber threats are costly: A successful cyber-attack can result in significant financial loss. This can include direct costs, such as the cost of fixing the problem, as well as indirect costs, such as lost business and damage to the company’s reputation.
- Cyber threats disrupt operations: A cyber-attack can disrupt business operations, which can result in lost productivity and revenue.
- Cyber threats can lead to data breaches: A successful cyber-attack can lead to a data breach, which can result in the loss or theft of sensitive information. This can have serious consequences for the business and its customers.
- Compliance: Many businesses are required to comply with various regulations and standards related to cybersecurity, such as ISO, CIS, or NIST. Implementing the Essential Eight can help organisations meet these requirements from the perspective of end users.
Overall, Essential Eight compliance is vital for businesses because it provides a solid foundation for protecting end users against cyber threats.
What are some Essential Eight strategies?
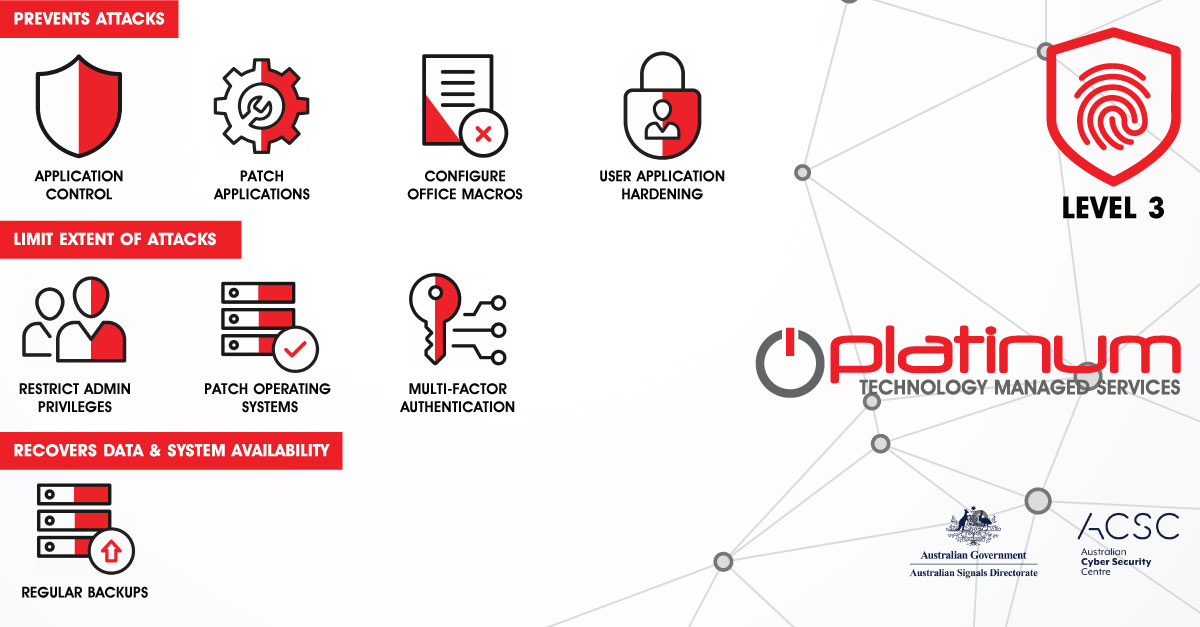
The Essential Eight strategies focus on eight key areas of defence:
- Application Control: Only allowing approved software to run
- Patch Applications: Regularly updating software to fix known vulnerabilities.
- Configure Microsoft Office Macros: Restricting the use of macros in Microsoft Office to prevent malware infections.
- User Application Hardening: Hardening web browser security settings and limiting extensions.
- Restrict Administrative Privileges: Limiting the number of users who have administrative access to a system.
- Patch Operating Systems: Regularly updating the underlying operating system to fix known vulnerabilities.
- Multi-factor Authentication: Using more than one form of authentication to confirm a user’s identity.
- Daily Backups: Regularly creating backups of data.
The Australian Cyber Security Centre (ACSC) encourages organisations to implement these Essential Eight strategies as a starting point (level 1 of 3) for improving their cyber security posture.
The Benefits of the Essential Eight Model
Benefits of implementing the Essential Eight strategies include:
- Increased security: By focusing on critical areas of defence, the Essential Eight helps organisations better protect themselves against known cyber threats.
- Reduced risk: Implementing Essential Eight strategies can help organisations to reduce their risk of falling victim to a cyber-attack.
- Better compliance: Many organisations are required to comply with various regulations and standards, such as the (as per compliance section above on previous page) Implementing the Essential Eight can help organisations to meet these requirements.
More Information on the Essential Eight
If you would like to know more about the Essential Eight, or speak to the experts about cyber security, contact Platinum Technology.
Platinum Technology is certified Level 3, the highest level for the Essential Eight program. Contact Platinum Technology via email or phone.
Platinum Technology specialises in helping medium to large sized organisations lower their IT costs, while improving their functionality, security, and stability.


